Securing Your Edge Control System: A Cybersecurity Framework
|
|
Time to read 5 min
|
|
Time to read 5 min
This guide provides a comprehensive cybersecurity framework for securing your edge control system. We'll explain why the stakes are dramatically higher when moving from monitoring to control, and detail a multi-layered, "defense-in-depth" strategy to mitigate these risks. From a hardened device foundation certified to IEC 62443 standards to secure network communications and a robust management plane, this framework is essential for deploying an edge control solution that is not only intelligent but fundamentally trustworthy.
Securing an edge control system is mission-critical, as a breach can lead to physical consequences, not just data loss.
A "defense-in-depth" strategy is essential, requiring three layers of security: the Device, the Network, and the Management Plane.
The hardware platform must be "secure-by-design," which can be verified by looking for vendor certifications like IEC 62443-4-1 and evidence of third-party penetration testing.
All remote communication must be encrypted via a VPN, and a properly configured firewall should isolate the sensitive OT network.
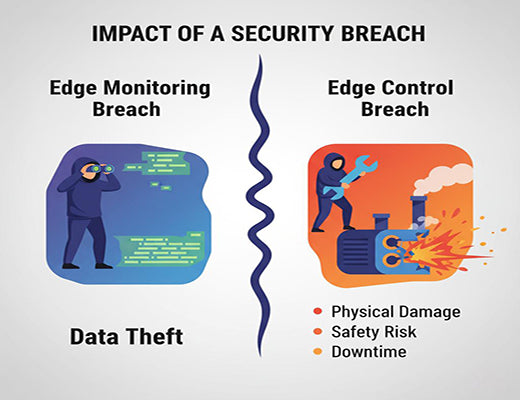
I was in a meeting with a Chief Information Security Officer (CISO). He told me, "An edge monitoring system getting hacked is a data breach. An edge control system getting hacked is a factory fire."
His statement perfectly captures the terrifying reality. When you give a device at the edge the power to not just see, but to act—to control a valve, to command a robot, to shut down a process—you elevate the cybersecurity stakes to the highest possible level.
Let's be clear: for a system with the power to affect the physical world, security cannot be an afterthought. It must be the foundational design principle. This guide will provide the framework for building a system that is secure by design.

To build a secure system, you must first understand the unique threats. An edge control system introduces a new level of risk compared to a simple monitoring setup.
Security starts with the physical device itself.
Once the device is secure, you must secure its communications.
Your cloud platform is your command center; its security is just as important.

In the high-stakes world of edge control, trust cannot be a feeling; it must be verifiable. You must demand proof of a vendor's security commitment. A secure system is born from a secure process, validated by independent experts, and operated with a security-first mindset. By building your solution on a platform that embraces this philosophy from the hardware up, you can harness the power of autonomous control with the confidence that your critical operations are safe and secure.
Further Reading:
What is Edge Control? The Future of Real-Time Industrial AutomationThe Software Stack for Edge Control: OS, Containers, and RuntimesCalculating the ROI of an Edge Control System: A Guide for Managers
A1: Overwhelmingly, the most common and dangerous vulnerability is the use of weak or default passwords on devices. Enforcing strong, unique passwords for every device and using multi-factor authentication on management platforms is the single most important security measure you can take.
A2: The IEC 62443 is a series of international standards focused on the cybersecurity of Industrial Automation and Control Systems (IACS). The IEC 62443-4-1 certification specifically focuses on the vendor's product development lifecycle, ensuring that security is a core requirement throughout the entire process.
A3: Zero Trust is a security model that assumes no user or device is inherently trustworthy, even if it's inside your network. It means every request to access a resource must be authenticated and authorized. In an edge control system, this means the gateway should not blindly trust a device on its local network; it must validate every connection and enforce strict firewall rules between different network segments.