A Guide to Access Control IoT Devices: Secure, Scalable, and Remotely Managed
|
|
Time to read 5 min
|
|
Time to read 5 min
A modern access control IoT devices system revolutionizes physical security by connecting your door controllers, card readers, and locks to the internet via a secure gateway. This guide explains how an IoT access control system works, moving management from a local, on-premise server to a powerful and flexible cloud platform. By leveraging a secure industrial router and a centralized management platform like RCMS, businesses can achieve granular remote control, real-time visibility, and enhanced security across all their locations.
An IoT access control system connects your on-site door hardware to a central cloud platform, enabling remote management and monitoring.
The key benefits are centralized control over multiple sites, enhanced security through real-time alerts and detailed audit trails, and improved operational efficiency by eliminating the need for physical key management.
The architecture consists of three parts: the on-site devices (readers, controllers), the secure connectivity hardware (an industrial router), and the cloud management platform (the brain).
Using a purpose-built industrial router with a hardened OS, firewall, and VPN is non-negotiable for securing your physical premises.
I was talking to an IT director for a fast-growing retail chain, and he was describing his "key nightmare." With 50 stores, he was drowning in a sea of physical keys, key cards, and disconnected, on-premise access control panels. An employee quits? He has to have a local manager reprogram the door. A break-in attempt over the weekend? He doesn't find out until Monday morning.
His problem wasn't a lack of locks; it was a lack of visibility and control.
Let's be clear: the era of isolated, on-premise security is over. The solution is to connect your doors to the cloud. The solution is a modern system built on access control IoT devices. This guide will break down how this technology works and how it can transform your physical security.

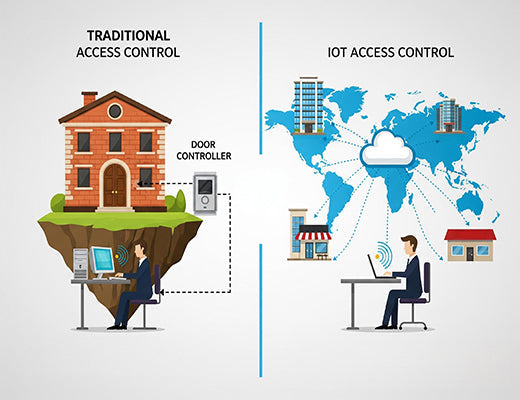
A traditional access control system has a controller and card reader at the door, but all the "brains" are on a server in a back closet. If you want to add a user or check an event log, you have to be physically on-site.
An IoT access control system takes that same on-site hardware but connects it to the internet through a secure gateway. This moves the "brains" of the system into the cloud. Now, that IT director can manage all 50 of his stores from a single web browser, from anywhere in the world.
The real 'aha!' moment for any multi-site manager is when they realize the immense operational benefits of centralizing control.
These are the familiar components at the door:
This is the most critical and often overlooked component. This is how your on-site panel securely connects to the cloud. Using a consumer-grade router here is a massive security risk. You need a purpose-built industrial router that acts as a secure bridge.
This is the new "brain" of your system. A platform like RCMS provides the user-friendly web interface to manage your entire system. This is where you:

The world of physical security is undergoing a profound digital transformation. By leveraging access control IoT devices and a robust connectivity platform, businesses can move beyond the limitations of isolated, on-premise systems. This modern approach delivers a solution that is not only more efficient and scalable but also fundamentally more secure, providing the real-time visibility and centralized control needed to protect your assets in today's connected world.

A1: This is a critical question. In a well-designed system, the local on-site access control panel still retains the necessary user credentials and logic. This means that even if the connection to the cloud is temporarily lost, employees with valid credentials can still access the building. All event logs are stored locally and will be synced with the cloud once the connection is restored.
A2: Yes, when implemented correctly, it is often more secure than an on-premise system. A professional cloud platform is hosted in a high-security data center with redundancies and is managed by security experts. The critical link is the connection from your site to the cloud, which is why using a secure industrial router with an encrypted VPN tunnel is non-negotiable.
A3: RBAC is a security model where access rights are assigned to roles rather than individual users. For example, you can create a "Sales Team" role that has access to the main office from 9 AM to 5 PM, and an "IT Admin" role that has 24/7 access to all doors, including the server room. When a new sales employee joins, you simply assign them the "Sales Team" role, and they automatically inherit the correct permissions. This is a core feature of a scalable management platform like RCMS.